Think of visiting an amusement park. At the entrance, you’re either handed a paper ticket that must be shown at every ride or you’re given a wristband that lets you move freely all day. Both methods prove you belong there, but each works differently.
That’s how web applications handle authentication. Some rely on session-based methods (the paper ticket), while others use JWTs (JSON Web Tokens) (the wristband). The choice depends on how much control, flexibility, and scale the application requires.
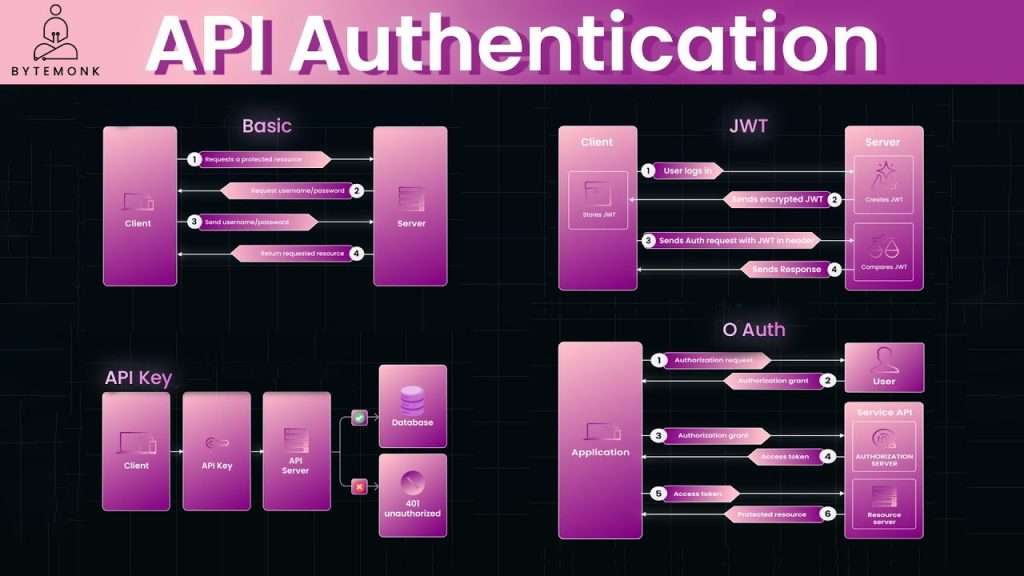
Session-Based Authentication: The Paper Ticket Style
With session-based authentication, every login creates a “record” stored on the server. The user gets a small ID—like a stub from the paper ticket—that they must show for each request. The server checks this stub against its list before granting access.
This method is secure and easy to revoke if needed. But as the number of users grows, it becomes harder to keep track of all the “tickets.” In large-scale systems or distributed setups, managing sessions across servers can get complicated.
Students in full stack classes are usually introduced to this first, since it’s the most traditional way of handling user identity and sets the stage for learning modern methods.
JWT Authentication: The Wristband Approach
JWTs change the game. Instead of the server storing user details, it issues a signed token—like a wristband with your information encoded into it. Each time you access a resource, you simply show the wristband, and the server verifies it without consulting a central list.
This approach is great for scalability. Distributed systems and APIs love JWTs because there’s no heavy “session book” to maintain. However, there’s a trade-off. If someone steals a token, it’s harder to revoke until it expires. That’s why JWTs are usually given short lifespans, with refresh tokens acting as backup passes.
Choosing What Fits Best
Should you use paper tickets or wristbands? The answer lies in what the “park” looks like.
- For smaller applications or systems needing close control, session-based methods are reliable.
- For larger ecosystems, like mobile apps or microservices, JWTs offer speed and flexibility.
- In many cases, teams blend the two—using JWTs for APIs while keeping sessions for browser-based logins.
The decision isn’t about which one is better universally but which one makes sense for the environment you’re building.
Strengthening Security
Regardless of the pattern, the real challenge is preventing fake tickets or wristbands from slipping in.
Best practices include:
- Enforcing HTTPS for all communication.
- Encrypting or hashing sensitive data.
- Setting session or token expiry times wisely.
- Using refresh tokens with JWTs.
- Monitoring login attempts for suspicious activity.
Hands-on practice in full stack classes often focuses on these scenarios. By working through projects, learners see how small design choices in authentication can lead to big differences in security.
Conclusion
Authentication is the gateway to every digital experience. Session-based patterns are like paper tickets—easy to check but harder to scale. JWTs are like wristbands—lightweight and scalable but requiring thoughtful safeguards.
The key is matching the method to the needs of the application. When chosen wisely and secured properly, both approaches create smooth, trustworthy user journeys.
In the end, it’s less about which system is “right” and more about designing the right balance of control, flexibility, and protection for the users you serve.